KERNEL - CYBERSECURITY SOLUTIONS
What is cybersecurity?
Cybersecurity is an important part of information security as applied to computers and networks. The objective of network security is to protect information and property from theft, corruption, or natural disaster while allowing the information and property to remain accessible and productive to their intended users.
- Confidentiality: is the term used to prevent the disclosure of information to unauthorised individuals or systems.
- Integrity: Information cannot be modified undetectably and without prior authorization.
- Availability: For any information system to serve its purpose, the information must be available when it is needed.
- Authenticity: It is necessary to ensure that the data, transactions, communications, or documents (electronic or physical) are genuine.
Cybersecurity risks are the threats and vulnerabilities that can compromise the confidentiality, integrity, and availability of digital information and systems. To protect against these risks, it's essential to implement effective security measures. Here's a brief overview of some common cybersecurity risk:
- Improper configured CyberSecurity Solutions:Misconfigurations, over permissive settings, too whide access to internet for critical systems, lack of visibility.
- Malware: Malicious software such as viruses, worms, and ransomware can infiltrate your systems.
- Phishing: Cybercriminals use deceptive emails or websites to trick users into revealing sensitive information.
- Weak Passwords: Weak or easily guessable passwords can be exploited by attackers.
- Insider Threats: Employees or contractors with malicious intent can pose a significant risk.
- Outdated Software: Unpatched software and systems may have known vulnerabilities.
- Data Breaches: Data breaches can lead to the exposure of sensitive information.
- DDoS Attacks: Distributed Denial of Service (DDoS) attacks can disrupt online services.
- Social Engineering: Attackers manipulate individuals into divulging confidential information.
- IoT Vulnerabilities:Internet of Things (IoT) devices can be entry points for cyberattacks.
- Lack of Employee Training:Inadequate cybersecurity awareness among employees can lead to security lapses.
- Supply Chain Vulnerabilities:Third-party vendors and suppliers can introduce risks.
- Inadequate Backup and Recovery:Without proper backups, data loss can occur or in of an incident the data cannot be restored.
- Shadow ITEmployees using unauthorized applications or services can bypass security measures.
- Improper tested Applications:Custom developed application that are not subjected to cybersecurity testing and analysis.
Kernel solutions:
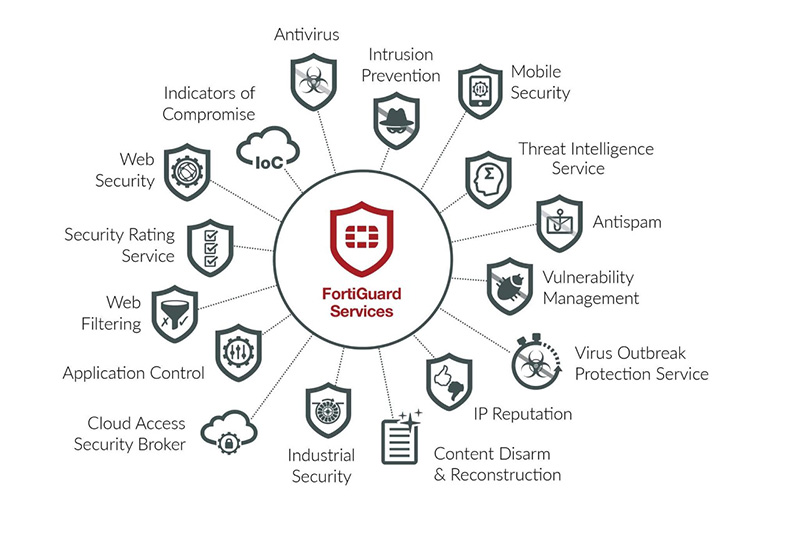
Security is a vast and continuous evolving field due to the continuous battle between cybercriminals that try to compromise and exploit the information and the security community that seeks to defend and safeguard it.
The profits, information and reputation are each day under threat by new and more advanced types of security attacks, facilitated by the continuous need of access and data exchange via internet.
The present economic downturn is also a source of instability due to the fact that potential disgruntled employees can act against the company interests for personal gain by selling or facilitating to the competition access to trade secrets and classified information.
Traditional security solution cannot longer provide adequate protection in the face of the new challenges.
Even if 100% security cannot be achieved without physical separation of the infrastructure, our solutions are mitigating the attacks and providing you the chance to focus on your core business without having to manage directly the security issues:
- The deployment of multi-layer security solutions can ensure that complex attacks are stopped at different points inside the infrastructure.
- Advanced intrusion prevention ensures that attacks against the applications can be stopped before they impact them.
- Application control and SSL inspection provides the organization with the capability to block less desirable applications for business and stop any potential remote control attacks against the infrastructure.
- Centralized log management can provide warning and data for the mitigation of the attacks.
- Antimalware, Anti-spam ensures that phishing attacks are stopped before the users are affected and have a chance to fall into the trap.
- Web filter boosts the productivity by eliminating the websites that are against the company policy or are bandwidth intensive.
- Web and database security ensures that potential application bugs or misconfigurations cannot be used as exploits for cyber-attacks.
- Remote secure access with strong encryption and authentication mechanisms is vital for the mobile sales force and for the integrity of the information exchanged.
- IP Telephony is protected against eavesdropping.
- End point protection ensures that no malicious activities are performed, no malware gets installed, computers are authenticated in the network (NAC) and the data that is used, is in compliance with the company policy and any deviation is logged.
- IP Video surveillance can ensure the physical security of you assets and limit the probability of loss by theft.



